BSides Charlotte was a great time and the people were fantastic. The CTF was awesome, because we (Mother Russia) won and had a blast with the Network King of the Hill-style competition.
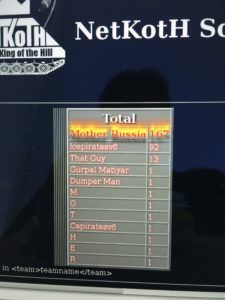
Great #1 Victory
Technical Details
So, I feel a little bit ashamed, but I spent the first hour and a half thinking that I was in netsec hell and was hitting a firewall or something, because NMAP was running extremely slowly (57 minutes for a /24), but it turned out that I was scanning an entirely wrong network.
After getting some good targets, I saw a lot of port 80. Most only had to default Apache pages, but one had a Drupal instance installed. The scoring mechanism required for teams to deface the front page of the web servers with <team>TeamName</team> tags, so this looked promising. My teammate pointed out that a Metasploit module existed for that version of Drupal (Drupalgeddon). In our case, it created an admin user and popped a meterpreter session with low privilege.
After logging in to the Drupal instance, it became clear that there was a lot of competition for the front page, but we used a secret weapon to swing the competition in our favor. Many teams were outright banning and blocking the other teams’ admin users, which I found to be a silly idea, because they would just create a new user and it would be a game of whack-a-mole. Instead of blocking or banning users, I simply removed their admin privileges, posted our flag and babysat the users page to remove new users’ permissions. After a while, even the facilitator of the CTF was asking how we were blocking access and assumed that we had rooted the box and were using IP Tables. Because it allowed for users to still browse all of the pages, many assumed that it was simply a network glitch when their posts didn’t work. As a result, they didn’t create new users and moved on the other targets, giving us a WIDE lead. The network was a target-rich environment, with quite a few open ports, but MS08-067 actually saved the day on quite a few of them. There were many boxes, but the Drupal incident was really my highlight of it all.
It was a fun CTF and a wonderful conference, so I want to give greetz to @th3mojo, @c0ncealed, and everyone who helped run @BsidesCLT.
